Enable logging
By default domain controllers only log successful login attempts, therefore you should first off all start logging failed login attempts. This is done via Group Policy:
Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Audit Policy
Enable both Success and Failure event logging for following Policies:
- Audit account logon events
- Audit account management
- Audit logon events
In theory it should be enough to apply above Group Policy settings only to your Domain Controllers, but it may be beneficial to have it applied to other computers as well. For example, if client is logging form a workstation to a terminal server, domain controller will log login attempts coming from the terminal server. But if you have “Audit logon events” enabled on terminal server itself, you will be able to see which workstation user is trying to login from.
Useful Event IDs (Server 2003 / Windows XP)
Domain Controllers
Event ID: 675
Category: Account Logon
Type: Failure Audit
Description: Pre-authentication failed
Event ID: 644
Category: Account Management
Type: Success Audit
Description: User Account Locked Out
Event ID: 540
Category: Logon/Logoff
Type: Success Audit
Description: Successful Network Logon
Event ID: 538
Category: Logon/Logoff
Type: Success Audit
Description: User Logoff
Servers and Clients
Event ID: 529
Category: Logon/Logoff
Type: Failure Audit
Description: Logon Failure. Unknown user name or bad password
Event ID: 539
Category: Logon/Logoff
Type: Failure Audit
Description: Logon Failure. Account locked out
Event ID: 528
Category: Logon/Logoff
Type: Success Audit
Description: Successful Logon
Event ID: 551
Category: Logon/Logoff
Type: Success Audit
Description: User initiated logoff
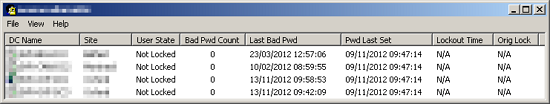
Lockout Status
Another potentially useful tool is Microsoft Account Lockout Status (LockoutStatus.exe). This utility displays lockout status for particular user account. Information is collected from every domain controller in your domain.
Tool can downloaded from here or directly from Microsoft.

Leave a Reply